Restrict Azure App Registration E-Mail Permission¶
Create E-mail Enabled Security Group¶
Go to Microsoft 365 Portal
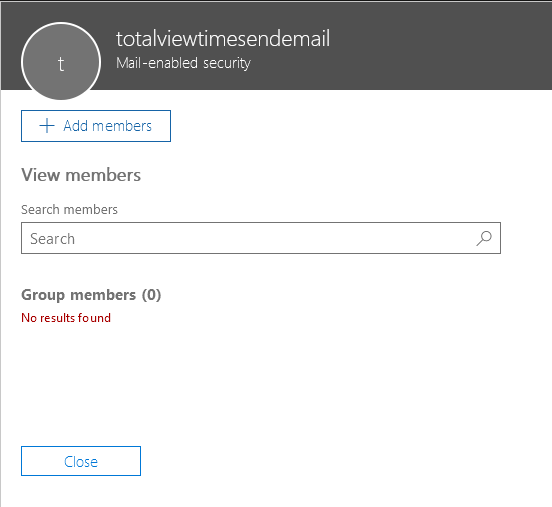
Create E-mail enabled security group, under Groups->Active Groups. Note that the e-mail address of the security group is not important. It will not be used as sender address or be visible anywhere to the receiver.
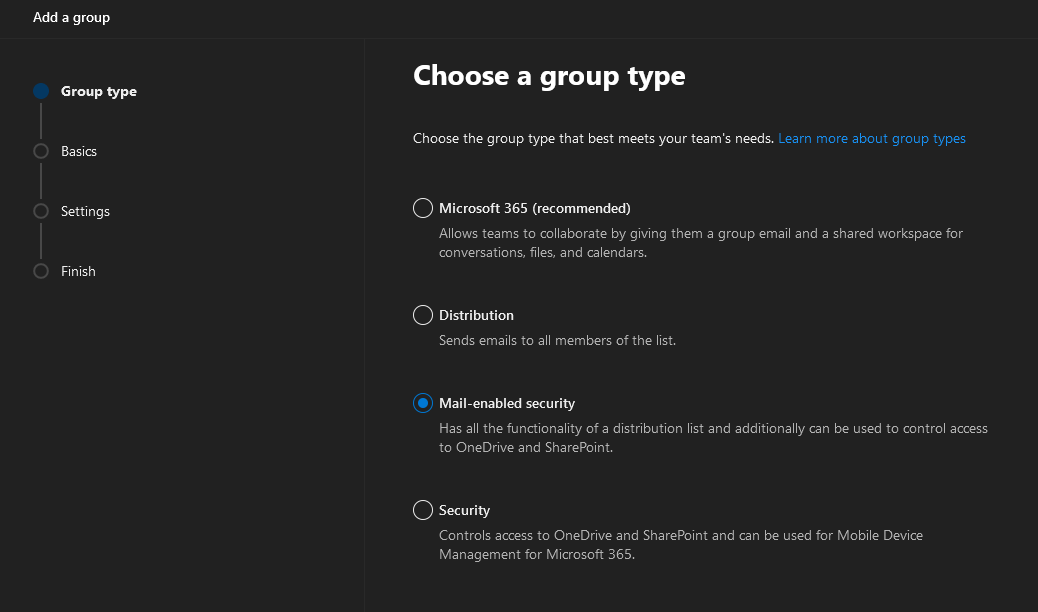
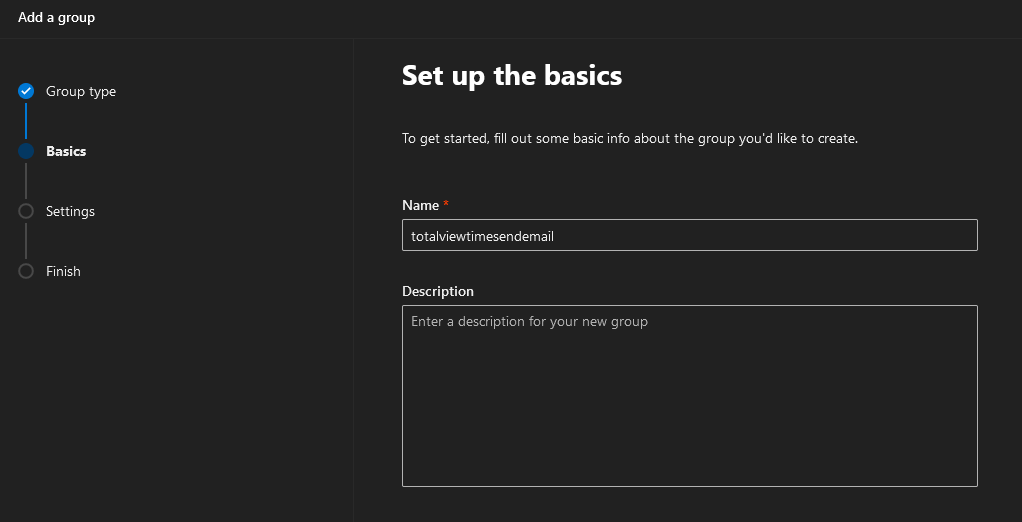
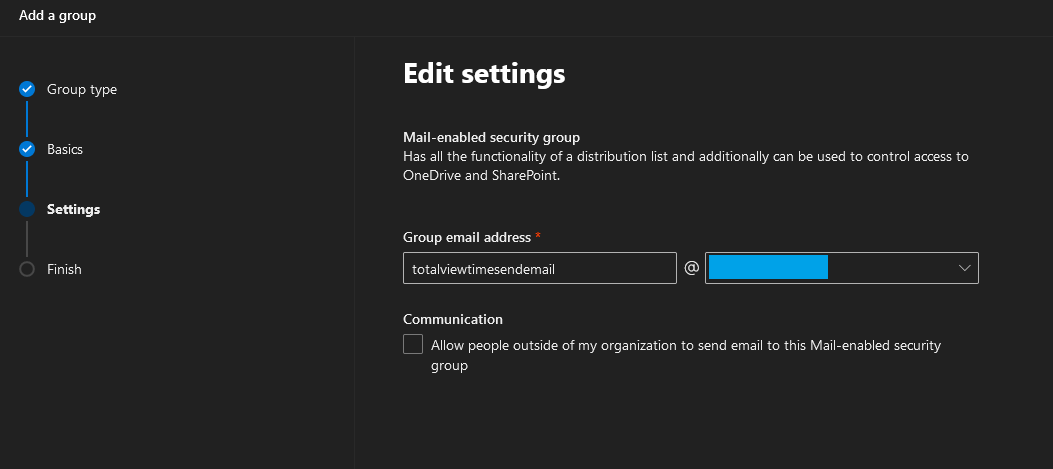
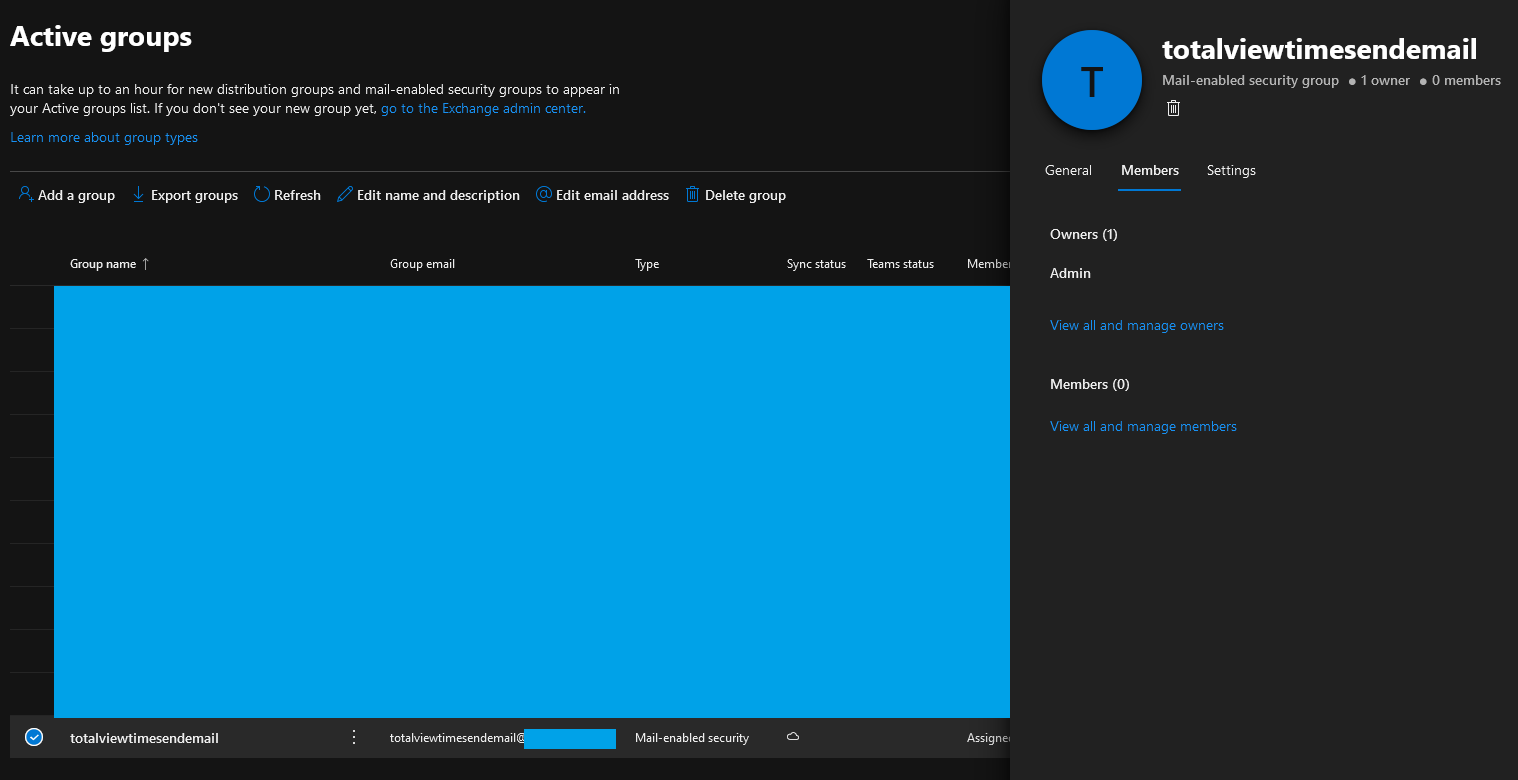
Wait for group to show up under active groups – it can take a few hours.
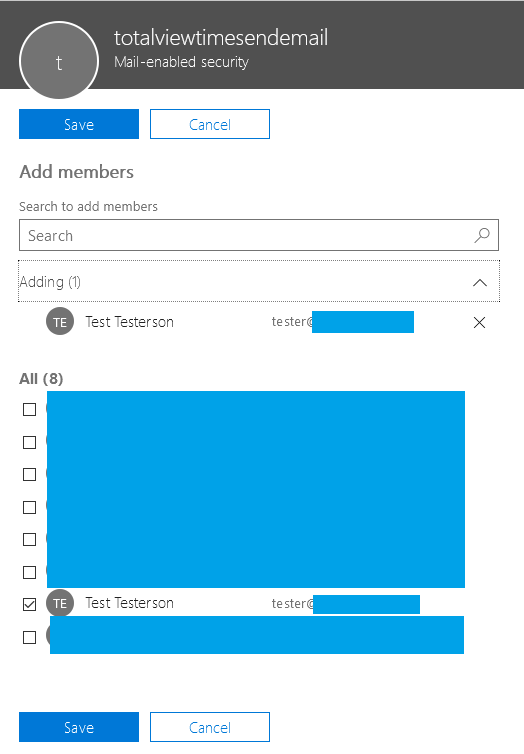
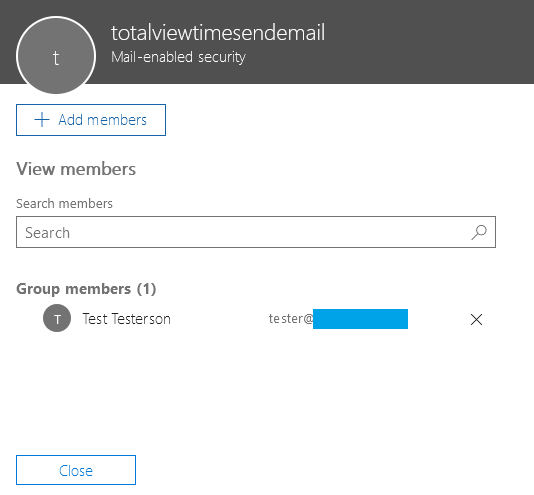
Once it shows up, add the e-mail address to it, that you want to be used as e-mail sender. This is the e-mail address that will be visible for the recipients, as sender address. The e-mail address can be a normal user’s mailbox, or it can be a shared mail box – which can be desirable, if you don’t want a dedicated e-mail account just for this functionality.
Install Exchange Online PowerShell V2 module¶
You need version 2.0.4 or newer of ExchangeOnlineManagement PowerShell module to be installed on your computer, in order to complete the configuration.
To test if you have ExchangeOnlineManagement PowerShell module, run the following command:
Get-InstalledModule -Name ExchangeOnlineManagement
If not installed, or version is older than 2.0.4, then run the following command to install:
Install-Module -Name ExchangeOnlineManagement
Run Get-InstalledModule again, to verify that installation was successful and see which version was installed:
Get-InstalledModule -Name ExchangeOnlineManagement
Note down the version number, as it will make a difference futher down in the guide.
Apply Application Access Policy to Azure App Registration¶
Open PowerShell to connect to Exchange Online.
If ExchangeOnlineManagement is version 2.0.4 or 2.0.5, then run the following, replacing <admin principal name> with the correct value:
Connect-ExchangeOnline -UserPrincipalName <admin principal name>
If ExchangeOnlineManagement is version 2.0.6 or newer, then run the following, replacing <admin principal name> with the correct value:
Connect-ExchangeOnline -UserPrincipalName <admin principal name> -UseRPSSession
Create new application access policy, limiting the App Registration to only be able to send e-mails for users that are members of the totalviewtimesendemail e-mail security group. Replace <Azure App Registration Client/App ID> and <your e-mail domain name> with the correct values:
New-ApplicationAccessPolicy -AppId <Azure App Registration Client/App ID> -PolicyScopeGroupId totalviewtimesendemail@<your e-mail domain name> -AccessRight RestrictAccess -Description "Restrict this app to members of distribution group totalviewtimesendemail."
Verification 1¶
To test if the created policy is taking effect, you can try running the following command, with different e-mail addresses in the domain:
Test-ApplicationAccessPolicy -Identity <test e-mail address> -AppId <Azure App Registration Client/App ID>

Verification 2¶
Open TotalviewExchange365.exe from <Totalview Installation Folder>\InstallFiles\Exchange365
Put in the Tenant ID, Client ID and Client Secret values and press “Test without Totalview”
Go to Send E-Mail tab and try sending an e-mail from an account that should not be permitted to send e-mails. It should fail.
Go to Send E-Mail tab and try sending an e-mail from an account that should be permitted to send e-mails. It should work.
If you experience that any of the last two steps are not working, try waiting two hours and retry. It can take a few hours for security restrictions to be enforced.
